Search results
Jump to navigation
Jump to search
Page title matches
- There are numerous classifications of '''network''' but, essentially, a network is a system of interconnected elements.132 bytes (17 words) - 12:05, 13 January 2024
- 12 bytes (1 word) - 12:03, 13 January 2024
- ...ections may be of short duration. A given element may move from network to network, or belong to several self-organizing networks.1 KB (160 words) - 12:12, 1 May 2024
- ...networks. A very similar concept applies in the Public Switched Telephone Network, where end office switches know how to reach directly connected telephones, ...ere is only one other network. The same rules apply on the 192.168.1.0/24 network.3 KB (465 words) - 07:36, 18 March 2024
- #REDIRECT [[Computer network]]30 bytes (3 words) - 09:29, 16 March 2010
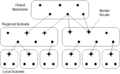
File:Network Hierarchy.png (650 × 400 (24 KB)) - 19:53, 11 March 2022- ...ture''', applicable to both [[telecommunications network]]s and [[computer network]]s as well as their continuing modern [[convergence of communications|conve #The separation of network functions into smaller pieces, which may be abstract [[layer (networking)|l607 bytes (83 words) - 09:46, 20 September 2009
- 72 bytes (8 words) - 17:00, 19 April 2010
- 12 bytes (1 word) - 12:38, 8 January 2009
- 12 bytes (1 word) - 19:22, 10 January 2010
- ...elecommunications provider that sells deregulated telephone service, under network neutrality, could not block or degrade a competitive [[voice over Internet ...le with the public Internet, although some could also be local to the FiOS network. <ref name=NW2010-08-08>{{citation15 KB (2,199 words) - 09:37, 5 August 2023
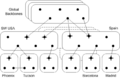
File:Network Hierarchy2.png (650 × 424 (26 KB)) - 19:57, 11 March 2022- 248 bytes (29 words) - 09:51, 20 September 2009
- 156 bytes (18 words) - 16:02, 23 April 2010
- ...mmunications]] is pushing the concepts of telecommunication and [[computer network]] to be interchangeable. ...communications network, although if one allows restrictions of information network, the set of public and private networks using the [[Internet Protocol Suite1 KB (147 words) - 17:26, 8 January 2009
- 38 bytes (5 words) - 10:41, 25 July 2009
- #REDIRECT [[Network topology]]30 bytes (3 words) - 00:16, 8 September 2008
- ...data encoding|data is encoded]], how [[medium access control|access to the network]] is handled, and how errors are [[acknowledgment schemes|reported]] and co ...t sensors or actuators that are very small and specialized computers. The network itself does not always require physical connections between participating d15 KB (2,278 words) - 05:21, 8 March 2024
- ...ceptable use policy. It also may be a precursor to external attacks on the network. ...ity monitoring when performed inside the boundaries of the network. Some [[network intrusion detection system]]s have difficulty in determining if a reconnais2 KB (356 words) - 05:49, 8 April 2024
- ...twork topology, and threw some rough diagrams up of a bus network and ring network. There's a lot more to add though... ...read academic and industry participation, the earliest networks, the early network marketplace, and then its evolution over time into what we have now. This18 KB (2,994 words) - 14:55, 18 April 2010
Page text matches
- ...hile [[Simple Network Management Protocol]] and [[syslog]] look inside the network elements286 bytes (37 words) - 10:15, 12 June 2009
- {{r|Public Switched Telephone Network}} {{r|Computer network}}341 bytes (42 words) - 14:19, 1 December 2010
- ...on the assumption that a packet entering a network must be forged, if the network has no return route to its source address203 bytes (33 words) - 00:13, 26 October 2009
- ...onfirmed attacking traffic is diverted, both for protecting the production network and for planning and executing a specific defense236 bytes (34 words) - 09:56, 12 June 2009
- ...n of technology-independent functions to be carried out by a specific real network331 bytes (37 words) - 09:49, 20 September 2009
- ...ture''', applicable to both [[telecommunications network]]s and [[computer network]]s as well as their continuing modern [[convergence of communications|conve #The separation of network functions into smaller pieces, which may be abstract [[layer (networking)|l607 bytes (83 words) - 09:46, 20 September 2009
- {{r|Computer network}} {{r|Telecommunications network}}331 bytes (41 words) - 22:45, 1 October 2009
- There are numerous classifications of '''network''' but, essentially, a network is a system of interconnected elements.132 bytes (17 words) - 12:05, 13 January 2024
- ...com/hijackers.html Social Network Analysis] of the [[9/11|9/11]] Terrorist Network115 bytes (14 words) - 08:06, 23 February 2024
- ...lvis Presley]], released on 22 November 1968, as the soundtrack to the NBC network's ''Elvis'' TV special.167 bytes (21 words) - 06:47, 23 March 2014
- ...spended in November 2010 for making campaign contributions in violation of network policy225 bytes (29 words) - 19:06, 5 November 2010
- ==Computer network security== ...ptable use policy]]. It also may be a precursor to external attacks on the network.1 KB (176 words) - 04:40, 26 September 2013
- ...ss of [[network reconnaissance]] techniques that may be part of legitimate network operations, or a probing to find vulnerabilities to attack182 bytes (25 words) - 09:55, 4 February 2009
- {{r|Computer network}} ===Routed network design===388 bytes (44 words) - 15:18, 31 October 2008
- ...mmunications]] is pushing the concepts of telecommunication and [[computer network]] to be interchangeable. ...communications network, although if one allows restrictions of information network, the set of public and private networks using the [[Internet Protocol Suite1 KB (147 words) - 17:26, 8 January 2009
- {{r|Local area network}} {{r|Network topology}}932 bytes (116 words) - 11:20, 9 December 2009
- ...ay be a legitimate operational function or a precursor to an attack on the network207 bytes (32 words) - 09:10, 4 February 2009
- ...that allows only one-way transmission, based on the number of users of the network.179 bytes (27 words) - 16:22, 8 January 2009
- {{r|Network architecture}} {{r|Repeater (local area network)}}425 bytes (53 words) - 10:00, 20 September 2009
- * [[Computer network]] * [[Global telephone network]] also known as the Public Switched Telephone Network [[PSTN]]694 bytes (57 words) - 07:46, 13 September 2020