Cloud computing: Difference between revisions
imported>Howard C. Berkowitz |
imported>Howard C. Berkowitz |
||
| Line 231: | Line 231: | ||
Public clouds are more efficient from the service provider standpoint, giving better resource utilization and potentially giving more opportunities for disaster recovery, but they present additional security concerns. Sometimes, there may simply be a regulatory requirement, such as HIPAA or PCI, which requires the application data to be on a server completely under the control, at least contractually, of the data owner. In other cases, there are technical security concerns, such as the potential ability of a virtual machine instance to snoop on a paused virtual machine instance of another computer, the paused image residing on the same physical server disk. | Public clouds are more efficient from the service provider standpoint, giving better resource utilization and potentially giving more opportunities for disaster recovery, but they present additional security concerns. Sometimes, there may simply be a regulatory requirement, such as HIPAA or PCI, which requires the application data to be on a server completely under the control, at least contractually, of the data owner. In other cases, there are technical security concerns, such as the potential ability of a virtual machine instance to snoop on a paused virtual machine instance of another computer, the paused image residing on the same physical server disk. | ||
===Public cloud=== | ===Public cloud=== | ||
In public clouds, access is over the Internet, although it may use per-session host-to-host security. The physical servers are shared among multiple customers of the cloud. | In public clouds, access is over the Internet, although it may use per-session host-to-host security and sometimes on-demand VPNs. The physical servers are shared among multiple customers of the cloud. | ||
===Private cloud=== | ===Private cloud=== | ||
Private clouds dedicate servers to specific customers or customer groups. Access may be by secure Internet session or over a [[virtual private network]]. | Private clouds dedicate servers to specific customers or customer groups. Access may be by secure Internet session or over a [[virtual private network]]. | ||
Revision as of 12:05, 14 March 2010
Cloud computing refers to accessing computing resources that are typically owned and operated by a third-party provider on a consolidated basis in data center locations. They feature on-demand provisioning and pay-as-you go resource billing, with minimal up-front investment. It is aimed at delivering cost-effective computing power over the Internet, including virtual private networks (VPN). Consumers of cloud computing services purchase computing capacity on-demand and are not generally concerned with the underlying technologies used to achieve the increase in server capability. These techniques, however, always include virtualization of processing capability.
Cloud services differ in their
- Delivery model: their user interface
- Deployment model: responsibility and sharing of infrastructure
In terms of the problem it solves, cloud networking is less new technology and more "a new deployment model." [1] It exploits that most servers are underutilized, and, if geographically distributed among multiple data centers, exploit time-of-day variations as well as the potential for improved failover.
Many commercial cloud offerings, however, are really no more than traditional managed hosting being marketed as clouds. While much of the trade press is legitimately concerned with security in the cloud, the issue of disaster recovery may be even more important. Several major cloud providers have had significant outages, which proved to be localized to a single physical data center — they had not exploited the inherent failover capabilities of some of the technologies that enable clouds. Being a "cloud" excuses neither the consumer or provider for, at the very least, the data protection and failover requirements of managed hosting.
It has similarities to a number of network-enabled computing methods, but some unique properties of its own. The core point is that users, whether end users or programmers, request resources, without knowing the location of those resources, and are not obliged to maintain the resources. The resource may be anything from low-level programming to a virtual machine instance, on which the customer writes an application, to Software as a Service (SaaS), where the application is predefined and the customer can parameterize but not program. Free services such as Google and and Hotmail are free SaaS, while some well-defined business applications, such as customer resource management as provided by Salesforce.com, are among the most successful paid SaaS applications. PayPal and eBay arguably are SaaS models, paid, at the low-end, on a transaction basis.
"What goes on in the cloud manages multiple infrastructures across multiple organizations and consists of one or more frameworks overlaid on top of the infrastructures tying them together. Frameworks provide mechanisms for:
- self-healing
- self monitoring
- resource registration and discovery
- service level agreement definitions
- automatic reconfiguration
"The cloud is a virtualization of resources that maintains and manages itself. There are of course people resources to keep hardware, operation systems and networking in proper order. But from the perspective of a user or application developer only the cloud is referenced[2]
It is, by no means, a new concept in computing. Bruce Schneier reminds us of that it has distinct similarities in the processing model, although not the communications model, with the timesharing services of the 1960s, made obsolete by personal computers. " Any IT outsourcing -- network infrastructure, security monitoring, remote hosting -- is a form of cloud computing."
The old timesharing model arose because computers were expensive and hard to maintain. Modern computers and networks are drastically cheaper, but they're still hard to maintain. As networks have become faster, it is again easier to have someone else do the hard work. Computing has become more of a utility; users are more concerned with results than technical details, so the tech fades into the background.[3]
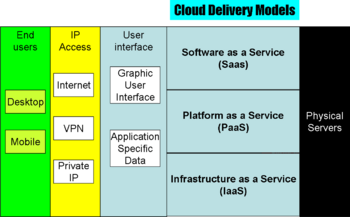
Delivery models
There is no single industry-accepted definition.[4] Some services broker extra capacity available on enterprise servers, as well as resources in pools of managed virtual servers. Others sell capacity on virtual servers. Yet others include any external computing resource, even to outsourced backup services, within the definition.
While the details of the service vary, some common features of sizing apply:
- Separation of application code from physical resources.
- Ability to use external assets to handle peak loads (not having to engineer for highest possible load levels).
- Not having to purchase assets for one-time or infrequent intensive computing tasks.
These definitions are converging, however, on three or four major models:
- Software as a Service (SaaS): the user interface is a human interface, usually a GUI, or a structured data exchange using XML or industry-specific file formats
- Platform as a Service (PaaS): customers program the cloud, but at a relatively high level, such as Web Services
- Infrastructure as a Service (IaaS): customers program the cloud, at a low level, either by a guest copy of an operating system on which they program, or, in some cases, at the low level of emulated hardware (e.g., block structured disk drivers)
- Data as a Service (DaaS): The cloud is more a repository than an active programming environment; often considered a subset of IaaS or sometimes PaaS, depending on whether the interface is to structured databases, files, or backup formats;
Software as a Service
Software as a Service appears to the user either as a Web-based graphic user interface, or as a data exchange format specific to an application. The most general type of application-specific data would be application-specific transactions, such as Health Level 7, which use a general data representation such as XML. Alternatively, the file format might only be understandable by the vendor's application.
One early and widely used SaaS application began with customer resource management by Salesforce.com. This allowed customer contact files, schedules, and other sales- and customer-interaction related information to be shared within an enterprise. The application provided a basic set of data entry forms and reports, with increasing levels of customization and functionality available at tiered prices. As Salesforce developed its product, [it merges into Platform as a Service by hosting third-party applications, which use SalesForce data, in a "SalesForce ecology".
Free email and search engines are SaaS, with limited customization, and sometimes premium offerings with more functionality. Some are advertising-supported, such as basic webmail services such as Hotmail and Gmail, Facebook. Free customers have no leverage with their cloud providers; there is very little recourse in the event of failures. Some vendors, however, have paid versions of these services, with higher levels of support and customization.
The second type of customer pays considerably for these services: to Salesforce.com, MessageLabs, managed network companies, and so on. These customers have more leverage, providing they write their service contracts correctly. With both types, the customer has very little disaster recovery capability since the applications only are available on the vendor's servers.
Quite a few business services are really SaaS, such as PayPal and eBay; they are services to facilitate transactions between users. The creation of various credit card and check payment features are examples of how SaaS can be customized without programming. Especially in areas where there are significant compliance requirements, such as the Payment Card Industry for credit cards, SaaS providers such as Savvis also offer professional services. [5]
Since the workload per user is highly predictable, billing for SaaS tends to be on a "per-seat" basis of a charge per registered user per month.
Platform as a Service
Similar to SaaS in that the user interface is web-based, but differing in that programming, at a higher level of abstraction than in utility computing, is necessary. Some are restricted to an business function specific set of APIs (e.g., Strike Iron and Xignite) to a wider range of APIs in Google Maps, the U.S. Postal Service, Bloomberg, and even conventional credit card processing services. Billing for PaaS is most commonly on a per-transaction model.
Salesforce.com now offers an application-building system with this term, called Force.Com, as well as its original SaaS products. [6] Google App Engine is here. Mashup-specific platforms include Yahoo Pipes or Dapper.net.
StrikeIron, for example, might be considered a computer-to-computer mashup, integrating external data bases with enterprise data, and combining them within a common business functions such as call centers, customer resource management and eCommerce. It refers to its offering as "Data as a Service", and accepts some of the data sources described above, such as the U.S. Postal Service. [7]. Xignite is more specific to the financial industry, retrieving data such as stock quotes, financial reference data, currency exchange rates, etc.
Web service clouds
- See also: Web services
The APIs come from the framework of Web services, but they are front-ended with proprietary software development tools.
Java clouds
A Java Virtual Machine is middleware, not the operating systems or virtual processors in IaaS. There is differentiation among the offerings. Nikita Ivanov describes two basic approaches, which are not mutually exclusive, but different products tend to have one or the other dominate. [8] The first is much like the way a traditional data center is organized, where the developers have little control over infrastructure. "The second approach is something new and evolving as we speak. It aims to dissolve the boundaries between a local workstation and the cloud (internal or external) by providing relative location transparency so that developers write their code, build and run it in exact the same way whether it is done on a local workstation or on the cloud thousands miles away or on both."
Cloudsafe points out that for digital content, such as video, one uses an application to access it, not the file system. "If your application is housing your metadata, and only object storage is required, the Simple Object interface can be accessed with either a Java SDK, or HTTP/REST API... the resulting object ID is stored directly within the application." Filesystem interfaces are available if needed, as with loading content.[9]
Elastic Grid adds value to a Java virtual machine platform with what they call a "Cloud Management Fabric" and a "Cloud Virtualization Layer".[10] The latter provides Elastic Grid customers with an overlay onto IaaS providers such as Amazon EC2 and Rackspace. The former allows the customer to "dynamically instantiate, monitor & manage application components. The deployment provides context on service requirements, dependencies, associations and operational parameters."
Python Virtual Machine
Google App Engine is a virtual machine that runs Python.
Cloud integration
Inter-cloud linkage, perhaps to allow business-to-business rather than user-to-service functionality; this has also been called Enterprise Service Bus. Vendors in this space, such as Rearden Commerce and Ariba, are brokers between customers and service providers.
Cloud integration comes, at least in part, from virtualization vendors. A Gartner Group analyst, Cameron Haight, says it is really several years away, with issues such as how "one cloud provider can consume the metadata associated with a virtual machine from another vendor," the metadata describing the service requirements of that virtual machine. There is a controversy over the business approach taken by VMWare, whose management tools will support only its own hypervisor, as opposed to the more general approach of Citrix and Microsoft.[11] Red Hat is also moving into the virtualization market, with cloud integration, through the open source project called DeltaSource.org, to facilitate private-public cloud integration. [12]
There are over 1,000 vendors of VMware's vSphere, including AT&T, Savvis and Verizon Business. VMware is offering its vCloud API to the Desktop Management Forum, which they say is responsive to open standards. An industry analyst, Chris Wolf of the Burton Group, said that making the API available without the infrastructure is marketng, not interoperability.[11]
Infrastructure as a Service
Amazon.com, Sun, IBM, and others who now offer storage and virtual servers that IT can access on demand to virtual application servers, while others build virtual datacenters with multiple servers (e.g., 3Tera's AppLogic and Cohesive Flexible Technologies' Elastic Server on Demand. Liquid Computing's LiquidQ offers similar capabilities, enabling IT to stitch together memory, I/O, storage, and computational capacity as a virtualized resource pool available over the network. The charging model is based on the use of resources, such as processing time, memory, and mass storage.
Amazon Elastic Compute Cloud (Amazon EC2) is a cloud offering on which customer developers write application on a wide assortment of virtual machines, which the customer builds from choices among operating systems, data bases, web servers, etc. [13]
The first category tends to be for highly interactive applications, so the computational load is less on-demand and less dynamic. The cloud extensions, therefore, tend to be things such as consoles, plugins, and management consoles that either run or do not run, rather than require resource tuning.
The second does not require human interaction, so can be more on-demand and need more sophisticated resource management. Applications here might be mail service provider infrastructure outsourcing, data mining, etc.
Some cloud computing applications do try to replicate compute-intensive supercomputer applications using highly distributed parallel processsing. [14]
A few data center vendors are targeting cloud providers, allowing them to dynamically configure systems of physical servers, as required by their customer demand, but not requiring they construct a data center.
While not necessarily marketed as clouds, certain infrastructure services, such as Domain Name System, are available as on-demand services. Messaging services that may be outsourced are broader than email, especially when there are regulatory requirements for archiving, audit or security.
Messaging
Messaging services are inherently distributed, and now extend to service beyond email, such as short message services such as texting, and pager services. When sent in a corporate context, for example, instant messaging services may be less formal to the user than email, but still need to be archived for possible litigation or law enforcement discovery.
Outsourced services that are commercially available meet different sets of customer needs for the same basic messaging functions. Archiving is a basic function, but a public company under Sarbanes-Oxley Act regulation will need more rigorous archiving than a small business.[15]
Data as a Service
Cloud storage is a model of networked data storage where data is stored on multiple virtual servers, generally hosted by third parties, rather than being hosted on dedicated servers.[16]There are cloud storage service for the small and home office market, such as Carbonite (backup)[17] and MozyHome (backup).
Even the consumer services differentiate, from being a "flash drive in the cloud" to offering encryption, incremental backups, data sharing, etc. There are high-end massive data backups, as well as federated data bases.
Messaging archives are another form of DaaS. A basic archive simply provides for backup. A more complex service, which includes not only infrastructure services but specialized end user services such as legal compliance (e.g., compliance and discovery) can be delivered with clouds.
- Barracuda Message Archiver [18]
- Dell, for example, offers a "Rapid Archive", and an "Enterprise Archive" meant for large companies
- Postini [19]
Especially with a distributed workforce, it may be wise to have messaging service that will continue to operate if a customer-owned server fails, or even if the data center is put out of service by a disaster. Various commercial services provide backup email services with standard protocols such as Simple Mail Transfer Protocol, Post Office Protocol, and Internet Message Access Protocol; proprietary servers with mixed proprietary and standard protocols such as Microsoft Exchange; and end user access such as webmail, Blackberry or other personal devices and text-to-speech. This may be done purely for disaster recovery, but also can be for legal reasons of compliance or discovery, and for cheaper storage of old data.
- Barracuda Backup Service[20]
- Dell EMS Continuity Service
Underlying architecture
Internally, cloud computing almost always uses several kinds of virtualization. The application software will run on virtual machines, which can migrate among colocated or networked physical processors.
For full generality, Citrix CEO Simon Crosby said customers shouldn't have "to ask the cloud vendor whose virtual infrastructure platform was used to build the cloud. Citrix supports the Xen open source hypervisor. Amazon and Rackspace use Xen. Network World does suggest that Citrix, with its smaller market share, must support other hypervisors including VMware and Microsoft, while the reverse is not true.[11]
The customer interface to the VM may be deliberately machine- and OS-independent (e.g., Java virtual machine), or virtualized operating system instances.
From the provider perspective, some of the advantages of offering cloud, rather than more conventional services, include:
- Sharing of peak-load capacity among a large pool of users, improving overall utilization.
- Separation of infrastructure maintenance duties from domain-specific application development.
- Ability to scale to meet changing user demands quickly, usually within minutes
For reasons of commercial reliability, however, the resources will rarely be consumer-grade PCs, either from a machine resource or form factor viewpoint. Disks, for example, are apt to use Redundant Array of Inexpensive Disks technology for fault protection. Blade server, or at least rack mounted server chassis will be used to decrease the data center floor space, and often cooling and power distribution, complexity. These details are hidden from the application user.
The cloud provider can place infrastructure in geographic areas that have reduced costs of land, electricity, and cooling. While Google's developers may be in Silicon Valley, the data centers are in rural areas further north, in cooler climates.
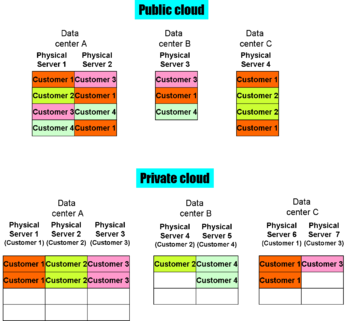
Deployment models
Deployment models, at their most basic, deal with whether a physical server can be shared among multiple customers. This can be challenging when the cloud provider actually uses another cloud for infrastructure; the first provider must make verifiable contract arrangements with the second to ensure server separation.
Public clouds are more efficient from the service provider standpoint, giving better resource utilization and potentially giving more opportunities for disaster recovery, but they present additional security concerns. Sometimes, there may simply be a regulatory requirement, such as HIPAA or PCI, which requires the application data to be on a server completely under the control, at least contractually, of the data owner. In other cases, there are technical security concerns, such as the potential ability of a virtual machine instance to snoop on a paused virtual machine instance of another computer, the paused image residing on the same physical server disk.
Public cloud
In public clouds, access is over the Internet, although it may use per-session host-to-host security and sometimes on-demand VPNs. The physical servers are shared among multiple customers of the cloud.
Private cloud
Private clouds dedicate servers to specific customers or customer groups. Access may be by secure Internet session or over a virtual private network.
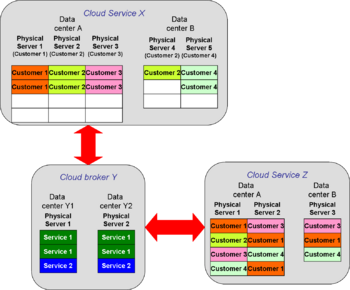
Hybrid cloud
Hybrid clouds are made up of interconnected private or public clouds. Interconnection may run through a third, mutually trusted cloud. In the illustration, assume the private cloud is a set of banks, which may, in fact, run their own clouds. The public cloud might serve e-commerce providers, hosting their websites. The broker, Y, is a payment clearinghouse, trusted by both sides.
Alternatively, the broker could be a wholesaler for private content providers, such as pay-for-view entertainment.
In a hybrid cloud, the private networks can maintain their own security policies. If they have a compliance overseer, that organization can audit the broker much more easily than auditing all the possible untrusted-to-trusted relationships.
There are no particular connectivity assumptions about hybrid clouds, although all links to the broker are apt to be secure, and the links to the private clouds are more likely to be on secure VPNs or even private IP networks.
Security and trust
Security, which includes availability, confidentiality and integrity may well be the greatest obstacle to deploying cloud technology. It simply may not be possible for the user to audit and control certain security mechanisms in the cloud. There is a spectrum of risk-benefit: few would worry about the read-only webcam that shows a view of the nearby harbor being on any cloud; few would accept a military system that controls the use of nuclear weapons being on other than a highly isolated network.
In other words, it is probably realistic to say clouds, as of early 2010, are secure enough for some missions but not others. The security implementations for some purposes simply are not sufficiently mature. Trust and audit, however, is a broader issue than security controls alone.
Trust, however, is not only a cloud issue. Alan Murphy points out that to get the benefits of clouds, one has to trust the providers for certain things, but doing so continues a trend in information technology. "I have to modify my level of trust, and apply new and stronger safeguards to the rest of my workflow processes (personal and professional) to make sure I’m able to recover if/when there is a massive breach that’s beyond my control. My recovery is something I can control, and I definitely trust myself." In his early work, he did detailed on-site audits of traditional physical data centers.
What I took from that multi-year experience: It’s extremely expensive to conduct these types of audits, and at some point the liability baton is passed to the people actually implementing the technology, away from those who designed it. I could interview people all day, and spend weeks walking through their network, but once I left the premises and filed my report, it was up to them to stick to those procedures. We had to trust (in our case legally) that what I saw remained in place...in the cloud model, we have to trust so many new components in the stack. Of course we can have safeguards (SSL) and checks and balances (pen-tests, people who responsibly disclose security flaws) but at a minimum, those require near unfettered access to systems that are no longer in our control and require knowledgeable people to address them. In my auditing days I had unfettered access, during a specific window of time. Once I was done my access went away.[21]
Various sectors and industries have compliance requirements, such as Payment Card Industry Data Card Standard (PCI DSS), HIPAA in health care, and FISMA in the U.S. Government. There are no general answers if cloud computing can be trusted for compliance, but analysis may show some customer-cloud combinations where it can, and some when it cannot. Several vendors have said they either are PCI DSS compliant, or, like Amazon, “in the process of, and will continue our efforts to obtain the strictest of industry certifications in order to verify our commitment to provide a secure, world-class cloud computing environment.” [22] Savvis describes PCI compliance in some detail; [23] Terremark states it is compliant but does not go into detail.
References
- ↑ V. Bertocci (April 2008), Cloud Computing and Identity, MSDN
- ↑ Kevin Hartig (15 April 2009), "What is Cloud Computing?", Cloud Computing Journal
- ↑ "Cloud Computing", Schneier on Security, June 4, 2009
- ↑ Eric Knorr, Galen Gruman (7 April 2008), What cloud computing really means
- ↑ SaaS: Seizing Opportunities, Meeting Challenges, Mitigating Risks, Saavis
- ↑ Force.com Platform, Salesforce.com
- ↑ Solutions, StrikeIron Data as a Service
- ↑ Nikita Ivanov, Java Cloud Computing - Two Approaches, GridGain Computing Platform
- ↑ Object Storage, Cleversafe
- ↑ Elastic Grid, Products
- ↑ 11.0 11.1 11.2 Jon Brodkin (31 August 2009), "VMware cloud initiative raises vendor lock-in issue", Network World, p. 1, 19
- ↑ John Fontana (31 August 2009), "Red Hat targets heavyweights in virtualization, cloud computing", Network World, p. 1, 24
- ↑ Amazon Elastic Compute Cloud (Amazon EC2), Amazon.com
- ↑ Aaron Ricadela (16 November 2007), "Computing Heads for Clouds", Business Week
- ↑ White paper: Solving On-Premise Email Management Services with On-Demand Services, Dell Modular Services, 2009
- ↑ Lucas Mearian (13 July 2009), "Consumers find rich array of cloud storage options: Which online service is right for you?", Computerworld
- ↑ About Carbonite, Carbonite Computer Company
- ↑ Barracuda Message Archiver, Barracuda Networks
- ↑ Simplify email retention with a central archive, Google Postini
- ↑ Barracuda Backup Service, Barracuda Networks
- ↑ Alan Murphy, "Cloud Computing: a New Level of Trust", Virtual Data Center
- ↑ Rich Miller (2 January 2009), "Can Cloud Computing Handle Compliance?", Data Center Knowledge
- ↑ Payment Card Industry (PCI) Data Assessment Solutions, Savvis