SIPRNET: Difference between revisions
imported>Howard C. Berkowitz (work in progress - snapshot) |
imported>Howard C. Berkowitz (Graphics and examples) |
||
| Line 16: | Line 16: | ||
* [[Defense Intelligence Agency]] | * [[Defense Intelligence Agency]] | ||
* [[Defense Information Systems Agency]] | * [[Defense Information Systems Agency]] | ||
Among their responsibilities, delegated to people on the Defense Information Systems Network Security Accreditation Working Group decide "who can connect when, where and how."<ref name=Reed> | Among their responsibilities, delegated to people on the Defense Information Systems Network Security Accreditation Working Group decide "who can connect when, where and how."<ref name=Reed /> | ||
==Getting connected== | ==Getting connected== | ||
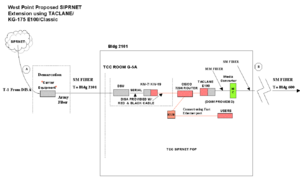
[[Image:SIPRNET POP access from West Point.png|left|thumb|Access from a base to a SIPRNET POP]] | |||
Not every military base has access to the SIPRNET backbone. For example, the [[United States Military Academy]] at [[West Point]], New York, has to run a secure link from its local SIPRNET facility to a SIPRNET [[point of presence]] (POP) on the SIPRNET backbone. | |||
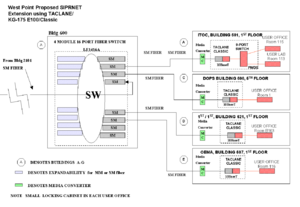
[[Image:West Point user access to SIPRNET.png|thumb|LAN user level access to SIPRNET]] | |||
From the router and other equipment that connects a location to the SIPRNET POP, the most common means of equipment is to connect the central base equipment to secure [[local area network]]s (LAN) on the campus. These LANs may themselves be encrypted, with each computer having its own encryption/decryption device, or the LANs may run through [[protected wireline distribution system]]s, which are judged to have sufficient physical protection that an adversary could not install a physical tap. | |||
==Human user access== | |||
Even though there are no special SIPRNET computers, there are authorized users. Every person with SIPRNET access must be approved by his or her chain of command, receive a user identifier, and have a [[password|strong password]] that is changed at least every 150 days. Think of a computer currently loggen in to SIPRNET as being like an unlocked safe with its drawers open; the user must not leave the logged-in computer. Even the [[United States Navy]], which runs on coffee, requires its users to log out before going to refill their coffee cups, and then log back in while sipping coffee. | |||
Apropos of coffee, wireless LAN connectivity such as offered by an Internet cafe is rarely if ever available, since access is harder to control. If it were approved, it would have to be in a building in which everyone is cleared to at least the SECRET level, and a sufficient guarded perimeter maintained around the building so it is technically impossible to log in from "outside the fence". Alternatively, there are approved products that provide an encrypted link between the end user and the wireless LAN router that connects to the local SIPRNET routing equipment. <ref>{{citation | |||
| url = http://images.telos.com/files/external/xacta_DSN_DS.pdf | |||
| author =Telos Corporation | |||
| title =Xacta Standard SIPRNET Deployable Wireless Node (XSDWN)}}</ref> | |||
While there are no SIPRNET-specific computers, there are rules covering computer use. All computers that have non-removable [[mass storage|disk drives]], which connect to SIPRNET, must be kept permanently in an area approved for having SECRET information in the open, such as a command post. A laptop with a hard drive, however, can be protected, when not in use, by locking it in a safe approved for SECRET material. | While there are no SIPRNET-specific computers, there are rules covering computer use. All computers that have non-removable [[mass storage|disk drives]], which connect to SIPRNET, must be kept permanently in an area approved for having SECRET information in the open, such as a command post. A laptop with a hard drive, however, can be protected, when not in use, by locking it in a safe approved for SECRET material. | ||
Revision as of 13:59, 15 July 2008
SIPRNET is the usual way to refer to the U.S. military's SECRET Internet Protocol Router Network. It is used used for passing tactical and operational information at the SECRET classification level. [1] SECRET is a medium level of security classification, and is the typical level for sensitive doctrine and procedures for regular military actions, orders for troop movement and even small to medium combat operations, after-action reports from conventional actions, resource inventories of personnel and ammunition, etc. Specifically, SIPRNET is generally restricted to "collateral" SECRET information, which does not have additional access restrictions. Access restrictions include such things as material specific to nuclear weapons, the details of some common intelligence systems, etc. Orders for major operations, the operational details and product of more exotic intelligence systems, etc., have to go on a network approved for more sensitive traffic, such as JWICS. SIPRNET, however, can handle the bulk of classified information used by conventional military units.
There is no such thing as a SIPRNET computer or terminal. SIPRNET is a network, and its users typically connect their computers to a local area network, which, through one or more routers and appropriate security equipment, connnect the worldwide secure network. This puts a good deal of responsibility on the user organizations to restrict physical access to LANs that interconnect with SIPRNET.
Management
Four Department of Defense agencies have joint responsibility for SIPRNET:
- Joint Staff J-6 communications-electronics directorate of the Joint Chiefs of Staff
- National Security Agency
- Defense Intelligence Agency
- Defense Information Systems Agency
Among their responsibilities, delegated to people on the Defense Information Systems Network Security Accreditation Working Group decide "who can connect when, where and how."[1]
Getting connected
Not every military base has access to the SIPRNET backbone. For example, the United States Military Academy at West Point, New York, has to run a secure link from its local SIPRNET facility to a SIPRNET point of presence (POP) on the SIPRNET backbone.
From the router and other equipment that connects a location to the SIPRNET POP, the most common means of equipment is to connect the central base equipment to secure local area networks (LAN) on the campus. These LANs may themselves be encrypted, with each computer having its own encryption/decryption device, or the LANs may run through protected wireline distribution systems, which are judged to have sufficient physical protection that an adversary could not install a physical tap.
Human user access
Even though there are no special SIPRNET computers, there are authorized users. Every person with SIPRNET access must be approved by his or her chain of command, receive a user identifier, and have a strong password that is changed at least every 150 days. Think of a computer currently loggen in to SIPRNET as being like an unlocked safe with its drawers open; the user must not leave the logged-in computer. Even the United States Navy, which runs on coffee, requires its users to log out before going to refill their coffee cups, and then log back in while sipping coffee.
Apropos of coffee, wireless LAN connectivity such as offered by an Internet cafe is rarely if ever available, since access is harder to control. If it were approved, it would have to be in a building in which everyone is cleared to at least the SECRET level, and a sufficient guarded perimeter maintained around the building so it is technically impossible to log in from "outside the fence". Alternatively, there are approved products that provide an encrypted link between the end user and the wireless LAN router that connects to the local SIPRNET routing equipment. [2]
While there are no SIPRNET-specific computers, there are rules covering computer use. All computers that have non-removable disk drives, which connect to SIPRNET, must be kept permanently in an area approved for having SECRET information in the open, such as a command post. A laptop with a hard drive, however, can be protected, when not in use, by locking it in a safe approved for SECRET material.
The more common practice is to keep all classified material on a removable storage unit, and only lock up the classified drive. Regular military precautions for using classified material, however, also require that the computer's random access memory must be erased, even with the removable disk disconnected, before the computer can leave a protected area. There is particular concern with regard to "thumb drives" and other small removable storage that a user inadvertently might take out of the protected area.
References
- ↑ 1.0 1.1 Reed, Kimberly K. (22 June 2004), SECRET Internet Protocol Router Network (SIPRNET)
- ↑ Telos Corporation, Xacta Standard SIPRNET Deployable Wireless Node (XSDWN)