User:David MacQuigg/Sandbox/Email security
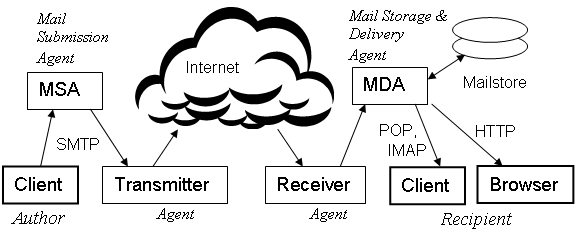
This article on Email security provides a brief overview of the ways in which email systems may be abused, and the many techniques that have been developed to fight that abuse. We begin by classifying the vulnerabilities according to what point in the system they may be localized. For easy reference, we repeat Figure 1 of Email system. We assume the reader is familiar with that article.
Client vulnerabilities
Infected workstation
After running a malicious program, perhaps from a phony website, the user's computer may become a zombie controlled by a remote criminal system. This can result in stolen passwords or other personal and financial data, or the sending of spam under the user's account.
Users should be trained to not run any programs that may infect their computer. Users should be required to maintain secure passwords.