Internetworking: Difference between revisions
imported>Dan Nessett (added gopher to pre-web internet apps) |
imported>Howard C. Berkowitz (Restoring old article, history lost, but hopefully we can start afresh) |
||
| Line 1: | Line 1: | ||
{{subpages}} | {{subpages}} | ||
{{TOC|right}} | {{TOC|right}} | ||
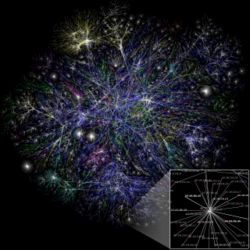
[[Image:Internet map 1024.jpg|right|thumb|250px|A map graphically displaying interconnections on the public Internet (known as [[Router|routes]]). These routes are managed via the dynamic [[routing protocol]] [[Border Gateway Protocol]]]] | |||
The '''Internet''' is a "network of [[computer network|networks]]" best known as the global network on which a wide range of applications and networking experiments runs, using technologies of the [[Internet Protocol Suite]]. | |||
To [[ | To the general public, the [[World Wide Web]] is the best-known application, but many other applications, such as electronic mail and a large percentage of telephone calls run over Internet protocols. Web browsers are perhaps the most common user programs that access the Internet, but web browsers translate human requests to the [[Hypertext Transfer Protocol]] that actually runs from browser to Web server. | ||
The Internet itself has no direct human interfaces; every user-visible function must go through a program resident on a client or server computer. There are literally hundreds of different [[protocol (computer)|protocols]], applications and services that run over the Internet. [[Virtual private network]]s interconnecting the parts of individual enterprises, or sets of cooperating enterprises, overlay the Internet. A wide range of interconnected networks using the same protocols as the public Internet, but isolated from it, provide services ranging from passing orders to launch [[nuclear weapon]]s, authorizing credit card purchases, collecting intelligence information, controlling the electric power grid (see [[System Control And Data Acquisition]]), [[telemedicine]] such as transferring medical images and even allowing remote surgery, etc. | |||
To Internet operators, however, the public Internet is the set of interconnected, separately administered networks, work through [[address registry|addressing registries]] to ensure unique addresses, and exchange information on reachability using the [[Border Gateway Protocol]] | |||
==Formative concepts== | |||
The first functional networks between individual computers were created in the early 1970s. These networks, however, assumed the computers ran common software and protocols. Some of the networks were proprietary to computer vendors, such as IBM's Binary Synchronous Communications and the 1974 System Network Architecture, Xerox Network Services, Digital Equipment Corporation DECnet. [[X.25]] was a nonproprietary standard, but used a different architecture than would the [[datagram]] networks such as the ARPANET and Internet. | |||
There were several intermediate steps between the ARPANET, to which access was strictly controlled, and today's ubiquitous Internet. See [[#History|History]] | |||
While IPv4 will be present indefinitely, it is limited in its capability for modern functions, and an evolution is in process to [[Internet Protocol version 6]] (IPv6). Internally, the Internet is divided into [[Autonomous System]]s, which exchange information about the destinations they can reach, using the [[Border Gateway Protocol]] (BGP). | |||
Louis Pouzin first introduced the idea of a generalized method of interconnecting networks of computers rather than individual computers, which he termed a '''catenet'''<ref name=Pouzin>{{citation | |||
| author = Pouzin, L. | |||
| title = A Proposal for Interconnecting Packet Switching Networks | |||
| conference = Proceedings of EUROCOMP | |||
| publisher = Bronel University | |||
| date = May 1974 | |||
| pages = 1023-36 | |||
| comment = not known to be online}}</ref>, but the model needed refinement. Such refinement took place under the sponsorship of the [[United States Department of Defense]]'s Advanced Research Project Agency (ARPA), later renamed the [[Defense Advanced Research Projects Agency]] (DARPA). ARPA was formed to meet a number of perceived Cold War technology challenges, and was established in 1958 as the first U.S. response to the Soviet launching of [[Sputnik]]<ref name="DARPA1">{{cite web|url=http://www.darpa.mil/body/overtheyears.html|title=Defense Advanced Research Projects Agency|publisher=United States government|year=2003|accessdate=2007-05-12}}</ref>. | |||
Among ARPA's areas of interest was the interconnection of networks, under the management and inspiration of J.C.R. Licklider 1915-1990<ref>{{citation | |||
| title = Internet Pioneers: J.C.R. Licklider | |||
| url = http://www.ibiblio.org/pioneers/licklider.html}}</ref>, one of the pioneers of cooperative research. Vint Cerf extended Pouzin's catenet model as the basis for what was to become the [[ARPANET]]:<blockquote>The U.S. | |||
DARPA research project on this subject has adopted the term to | |||
mean roughly "the collection of packet networks which are | |||
connected together." This is, however, not a sufficiently | |||
explicit definition to determine, for instance, whether a new | |||
network is in conformance with the rules for network | |||
interconnection which make the catenet function as confederation | |||
of co-operating networks.<ref name=CerfIEN48>{{citation | |||
| id = IEN 48 | |||
| title = The Catenet Model for Internetworking | |||
| first = Vint | last = Cerf | |||
| date = July 1978 | |||
| url = http://www.isi.edu/in-notes/ien/ien48.txt}}</ref></blockquote> | |||
===ARPANET=== | |||
Cerf extended the concept of catenet to be usable in a specific research network, the ARPANET. ARPANET was the first large-scale "network of networks" using common mechanisms to interconnect disparate networks. It was funded through ARPA, and access was limited to selected universities, research organizations, and government agencies. | |||
Contrary to widespread legend, it was never intended to be a military network survivable under nuclear attack, although other, not necessarily packet-switching, networks, were intended for warfighting. [[Paul Baran]], at the [[Rand Corporation]], is usually associated with the idea of survivable routed networks.<ref name=Baran-Dist101>{{citation | |||
| url = http://www.rand.org/pubs/research_memoranda/RM3420/ | |||
| author = Baran, Paul | |||
| id = Rand RM-3420-PR | |||
| title = On Distributed Communications: I. Introduction to Distributed Communications Networks | |||
| year = 1964}}</ref> Baran's extensive work influenced the development of packet switching, but there are distinctions between his contributions to the technology and to his solutions to specific military problems. | |||
High-availability, but not necessarily packet-switching, nuclear command networks started as early as the 1963 SACCS, specific to the [[Strategic Air Command]].<ref name=SAC>{{citation | |||
| title = Strategic Automated Command Control System | |||
| url = http://www.fas.org/nuke/guide/usa/c3i/saccs.htm | |||
}}</ref> Other warfighting networks included the even earlier Minimum Essential Emergency Command Network (MEECN), which was made up of multiple networks that were interconnected only through human intervention.<ref name=MinotMEECN>{{citation | |||
| first = Carla | last = Williams | |||
| date = 17 November 2005 | |||
| title = Minot completes final MEECN modifications | |||
| url = http://www.afspc.af.mil/news/story.asp?id=123024513}}</ref> Even today, the military warfighting networks, such as [[NIPRNET]], [[SIPRNET]], [[JWICS]] and [[Warfighter Information Network]] are separate from the Internet. | |||
Many educational institutions and corporations began joining the network, and in 1983 all nodes on the ARPANET changed over at once to [[Internet Protocol version 4]] (IPv4), which is still in use on the internet today. While this is often referred to as "TCP/IP", they are two distinct protocols: [[Transmission Control Protocol]] (TCP), and IPv4. In a literal sense the written term TCP/IP can be read aloud as "TCP over IP" and would be a correct description. | |||
===MILNET and its descendants=== | |||
In 1983, specifically military research, even though unclassified, split off the ARPANET into MILNET. There were gateways for specific projects, mostly from military to nonmilitary. Email could still pass fairly freely. There were a wide range of internal military networks using the technologies being researched. The research networks had their results shared, but the operational networks tended to suffer from the urban legend that people told about them had to die. | |||
Through several intermediate generations, MILNET essentially has become the unclassified [[NIPRNET]]. There are highly-interconnected networks for authorized users at various classified levels, including [[SIPRNET]] and [[JWICS]], which, at the user interface level, work much like the Internet. | |||
[[United States intelligence community]] networks, at the packet level, may or may not make use of the shared military networks. For various web- and wiki-like developments at the government-only and classified level, see [[Intellipedia]]. There are Intellipedia versions to which U.S. allies have access, at varying levels of sensitivity. | |||
===NSFNET=== | |||
The change to IPv4 allowed the next evolution, in 1984, to the [[NSFNET]], originally a U.S. government funded network that linked five supercomputer centers. At these centers, authorized research and academic users could connect their networks and access both the supercomputers and other resources. <ref name=NSFNET>{{citation | |||
| url=http://www.nsf.gov/about/history/nsf0050/internet/launch.htm | |||
| title = The Launch of NSFNET | |||
| author = National Science Foundation}}</ref> The centers were interconnected by what seemed, at the time, to be extremely fast 56 Kbps lines; 9.6 Kbps lines had been more of a limit for most other installations. Its [[Acceptable Use Policy]] (AUP) restricted it to use by authorized academic, research and government users; parallel networks with more open AUPs evolved, although organizations often needed separate connections. | |||
Routing in the NSFNET still had the concept of a hierarchy of core and regional networks. While completely obsolete now, the [[exterior routing protocol]] of the NSFNET was the Exterior Gateway Protocol (EGP), which evolved into the [[Border Gateway Protocol]] (BGP). BGP, now in Version 4, still can support hierarchy but is not restricted to it. | |||
== | ===ALTERNET=== | ||
In the early nineties, an increasing number of IP networks were commercially available, which connected to one another, and to NSFNET, in many ways both official and unofficial. ALTERNET was one. Other networks, not necessarily IP-based, connected to NSFNET, ALTERNET, or other networks via application-level gateways. In some cases, such as [[network news]], also called USENET, the specific application protocol was adapted to run over IP. In other cases, such as BITNET ("Because it's time" Network) or the academic CSNET, it might simply be an email, and possibly file, gateway. CSNET, incidentally, was NSF-funded, but for departments that did not meet the strict NSF requirements. | |||
Nevertheless, the Internet routed approximately same packets as today. The Internet of the time was not a fully public resource, and the research and academic users collaborated productively using electronic mail, file transfer, news, and other services. | |||
===Commercialization=== | |||
Before [[AOL]] opened up [[USENET]] and other Internet resources in the late 80s, the Internet was first an environment for networking research, and second an environment to support other research and education. When anonymous access became common, the social environment changed radically. The environment was one of trust as well as collaboration; anonymous access was rare. | |||
==Chronology== | |||
===1950s to 1970s=== | |||
In 1968, ARPA contracted with [[Bolt, Beranek and Newman]] to build the ARPANET Network Management Center and the Interface Message Processor (IMP) routers, although the term "router" had not yet been coined. | |||
The first testing of live [[ARPANET]] components started on August 30, 1969, when BBN delivered the first customer IMP to an ARPANET site ([[Leonard Kleinrock]]'s lab at UCLA). A one-IMP ARPANET was still meaningful, because it allowed testing of the host computer interface to the IMP. Installation of the second IMP at the Stanford Research Institute (SRI) on 29 October 1969, and testing of IMP-IMP protocols began: the first wide-area [[routing]] system. | |||
*[[ | |||
Among the first applications on the experimental networks was [[email]], on the ARPANET as well as vendor-proprietary networks and early commercial packet-switching networks such as [[TELENET]] and [[TYMNET]]. The latter networks used the [[X.25]] protocol that mimicked telephone calls, creating paths for each sender-receiver connection, as opposed to the connectionless Internet Protocol and its ancestors. Commercial email networks using X.25 were operational in 1972. | |||
*[[DARPA]] | |||
*[[BBN]] - Bolt, Beranek and Newman | |||
*[[NCP (ARPANET)]] | |||
[[Hypertext]] had been invented by [[Ted Nelson]] around 1960, and hyperdocuments could be transferred as files; [[Tim Berners-Lee]] later pioneered dynamic access to hyperdocuments on servers, which was the start of the [[World Wide Web]]. | |||
===1975 to 1980=== | |||
In 1979, the [[National Science Foundation]] established CSNET, to interconnect academic computer science departments and research institutions that were not eligible for ARPANET access. | |||
===1980 to 1985=== | |||
[[Tim Berners-Lee]], while a consulting engineer at CERN, wrote, for personal use, a program called ''Enquire''. Enquire can reasonably be considered the first networked hypertext application, although it certainly did not have the extensive indexing structure that characterizes the modern Web. | |||
Specifically military research split off the ARPANET into MILNET in 1983, although there was controlled access, mostly from military to nonmilitary. Email could still pass fairly freely. There were a wide range of internal military networks using the technologies being researched. The research networks had their results shared, but the operational networks tended to suffer from the urban legend that people told about them had to die. | |||
Without any intended Orwellian symbolism, the early, experimental ARPANET. in 1984, evolved to the [[NSFNET]], originally a U.S. government funded network that linked five supercomputer centers. At these centers, authorized research and academic users could connect their networks and access both the supercomputers and other resources. <ref name=NSFNET>{{citation | |||
| url=http://www.nsf.gov/about/history/nsf0050/internet/launch.htm | |||
| title = The Launch of NSFNET | |||
| author = National Science Foundation}}</ref> The centers were interconnected by what seemed, at the time, to be extremely fast 56 Kbps lines; 9.6 Kbps lines had been more of a limit for most other installations | |||
===1985 to 1990=== | |||
NSFNET did not allow commercial traffic, but there was a gradual creation of networks, often simple pairings, of various computers and networks over which traffic ineligible for the NSFNET passed. In the early nineties, an increasing number of IP networks were commercially available, which connected to one another, and to NSFNET, in many ways both official and unofficial. | |||
Nevertheless, the Internet routed approximately same packets as today. The Internet of the time was not a public resource, and the research and academic users collaborated productively using electronic mail, file transfer, news, and other services. | |||
Before [[AOL]] opened up [[USENET]] and other Internet resources in the late 80s, the Internet was first an environment for networking research, and second an environment to support other research and education. When anonymous access became common, the social environment changed radically. The environment was one of trust as well as collaboration; anonymous access was rare. | |||
[[Malware]] such as [[worm]]s and [[virus]]es were rare; the first well-known breakin happened in 1986,<ref>{{citation | |||
| author = Stoll, Cliff | |||
| title = The Cuckoo's Egg: Tracking a Spy Through the Maze of Computer Espionage | |||
| publisher = Pocket | year = 1989}}</ref> | |||
and the Morris worm hit in 1988.<ref>{{citation | |||
| contribution =Security of the Internet | |||
| title = The Froehlich/Kent Encyclopedia of Telecommunications vol. 15. | |||
| publisher =Marcel Dekker | |||
| year = 1997 | |||
| pages = 231-255 | |||
| url = http://www.cert.org/encyc_article/tocencyc.html}}</ref> | |||
1988 saw a major speed increase in NSFNET, going from what were then powerful and expensive 56 Kbps lines to 1.5 Mbps links more than 24 times faster. | |||
[[Tim Berners-Lee]] made the first proposal, in 1989, for the beginnings of a recognizable World Wide Web, based on his 1980 research on networked hypertext, which built on Ted Nelson's 1960 research on local hypertext. | |||
===1990 to 1995=== | |||
The ARPANET was officially turned off in 1990, but with many replacement networks. In 1990-1991, the general experience was that traffic, and especially the number of new network routes, was doubling approximately every five months, but router capacity was doubling every 18 months. [[Classless inter-domain routing]] (CIDR), a variant of IP, bought time for routers to catch up, by making routing more efficient. By 1995, Version 4 of the [[Border Gateway Protocol]], which fully supported CIDR, was operationa. | |||
NSFNET, which had essentially given up the [[Acceptable Use Policy]] of no commercial traffic, shut down in 1995. The National Science Foundation did create a new restricted IP network for supercomputing and high performance networking research, the Very High Speed Backbone Network Service (vBNS). | |||
==Impact on Society== | |||
===[[Netiquette]]=== | |||
==References== | ==References== | ||
{{reflist|2}} | {{reflist | 2}} | ||
Revision as of 22:50, 19 September 2009
The Internet is a "network of networks" best known as the global network on which a wide range of applications and networking experiments runs, using technologies of the Internet Protocol Suite.
To the general public, the World Wide Web is the best-known application, but many other applications, such as electronic mail and a large percentage of telephone calls run over Internet protocols. Web browsers are perhaps the most common user programs that access the Internet, but web browsers translate human requests to the Hypertext Transfer Protocol that actually runs from browser to Web server.
The Internet itself has no direct human interfaces; every user-visible function must go through a program resident on a client or server computer. There are literally hundreds of different protocols, applications and services that run over the Internet. Virtual private networks interconnecting the parts of individual enterprises, or sets of cooperating enterprises, overlay the Internet. A wide range of interconnected networks using the same protocols as the public Internet, but isolated from it, provide services ranging from passing orders to launch nuclear weapons, authorizing credit card purchases, collecting intelligence information, controlling the electric power grid (see System Control And Data Acquisition), telemedicine such as transferring medical images and even allowing remote surgery, etc.
To Internet operators, however, the public Internet is the set of interconnected, separately administered networks, work through addressing registries to ensure unique addresses, and exchange information on reachability using the Border Gateway Protocol
Formative concepts
The first functional networks between individual computers were created in the early 1970s. These networks, however, assumed the computers ran common software and protocols. Some of the networks were proprietary to computer vendors, such as IBM's Binary Synchronous Communications and the 1974 System Network Architecture, Xerox Network Services, Digital Equipment Corporation DECnet. X.25 was a nonproprietary standard, but used a different architecture than would the datagram networks such as the ARPANET and Internet.
There were several intermediate steps between the ARPANET, to which access was strictly controlled, and today's ubiquitous Internet. See History
While IPv4 will be present indefinitely, it is limited in its capability for modern functions, and an evolution is in process to Internet Protocol version 6 (IPv6). Internally, the Internet is divided into Autonomous Systems, which exchange information about the destinations they can reach, using the Border Gateway Protocol (BGP).
Louis Pouzin first introduced the idea of a generalized method of interconnecting networks of computers rather than individual computers, which he termed a catenet[1], but the model needed refinement. Such refinement took place under the sponsorship of the United States Department of Defense's Advanced Research Project Agency (ARPA), later renamed the Defense Advanced Research Projects Agency (DARPA). ARPA was formed to meet a number of perceived Cold War technology challenges, and was established in 1958 as the first U.S. response to the Soviet launching of Sputnik[2].
Among ARPA's areas of interest was the interconnection of networks, under the management and inspiration of J.C.R. Licklider 1915-1990[3], one of the pioneers of cooperative research. Vint Cerf extended Pouzin's catenet model as the basis for what was to become the ARPANET:
The U.S.
DARPA research project on this subject has adopted the term to mean roughly "the collection of packet networks which are connected together." This is, however, not a sufficiently explicit definition to determine, for instance, whether a new network is in conformance with the rules for network interconnection which make the catenet function as confederation
of co-operating networks.[4]
ARPANET
Cerf extended the concept of catenet to be usable in a specific research network, the ARPANET. ARPANET was the first large-scale "network of networks" using common mechanisms to interconnect disparate networks. It was funded through ARPA, and access was limited to selected universities, research organizations, and government agencies.
Contrary to widespread legend, it was never intended to be a military network survivable under nuclear attack, although other, not necessarily packet-switching, networks, were intended for warfighting. Paul Baran, at the Rand Corporation, is usually associated with the idea of survivable routed networks.[5] Baran's extensive work influenced the development of packet switching, but there are distinctions between his contributions to the technology and to his solutions to specific military problems.
High-availability, but not necessarily packet-switching, nuclear command networks started as early as the 1963 SACCS, specific to the Strategic Air Command.[6] Other warfighting networks included the even earlier Minimum Essential Emergency Command Network (MEECN), which was made up of multiple networks that were interconnected only through human intervention.[7] Even today, the military warfighting networks, such as NIPRNET, SIPRNET, JWICS and Warfighter Information Network are separate from the Internet.
Many educational institutions and corporations began joining the network, and in 1983 all nodes on the ARPANET changed over at once to Internet Protocol version 4 (IPv4), which is still in use on the internet today. While this is often referred to as "TCP/IP", they are two distinct protocols: Transmission Control Protocol (TCP), and IPv4. In a literal sense the written term TCP/IP can be read aloud as "TCP over IP" and would be a correct description.
MILNET and its descendants
In 1983, specifically military research, even though unclassified, split off the ARPANET into MILNET. There were gateways for specific projects, mostly from military to nonmilitary. Email could still pass fairly freely. There were a wide range of internal military networks using the technologies being researched. The research networks had their results shared, but the operational networks tended to suffer from the urban legend that people told about them had to die.
Through several intermediate generations, MILNET essentially has become the unclassified NIPRNET. There are highly-interconnected networks for authorized users at various classified levels, including SIPRNET and JWICS, which, at the user interface level, work much like the Internet.
United States intelligence community networks, at the packet level, may or may not make use of the shared military networks. For various web- and wiki-like developments at the government-only and classified level, see Intellipedia. There are Intellipedia versions to which U.S. allies have access, at varying levels of sensitivity.
NSFNET
The change to IPv4 allowed the next evolution, in 1984, to the NSFNET, originally a U.S. government funded network that linked five supercomputer centers. At these centers, authorized research and academic users could connect their networks and access both the supercomputers and other resources. [8] The centers were interconnected by what seemed, at the time, to be extremely fast 56 Kbps lines; 9.6 Kbps lines had been more of a limit for most other installations. Its Acceptable Use Policy (AUP) restricted it to use by authorized academic, research and government users; parallel networks with more open AUPs evolved, although organizations often needed separate connections.
Routing in the NSFNET still had the concept of a hierarchy of core and regional networks. While completely obsolete now, the exterior routing protocol of the NSFNET was the Exterior Gateway Protocol (EGP), which evolved into the Border Gateway Protocol (BGP). BGP, now in Version 4, still can support hierarchy but is not restricted to it.
ALTERNET
In the early nineties, an increasing number of IP networks were commercially available, which connected to one another, and to NSFNET, in many ways both official and unofficial. ALTERNET was one. Other networks, not necessarily IP-based, connected to NSFNET, ALTERNET, or other networks via application-level gateways. In some cases, such as network news, also called USENET, the specific application protocol was adapted to run over IP. In other cases, such as BITNET ("Because it's time" Network) or the academic CSNET, it might simply be an email, and possibly file, gateway. CSNET, incidentally, was NSF-funded, but for departments that did not meet the strict NSF requirements.
Nevertheless, the Internet routed approximately same packets as today. The Internet of the time was not a fully public resource, and the research and academic users collaborated productively using electronic mail, file transfer, news, and other services.
Commercialization
Before AOL opened up USENET and other Internet resources in the late 80s, the Internet was first an environment for networking research, and second an environment to support other research and education. When anonymous access became common, the social environment changed radically. The environment was one of trust as well as collaboration; anonymous access was rare.
Chronology
1950s to 1970s
In 1968, ARPA contracted with Bolt, Beranek and Newman to build the ARPANET Network Management Center and the Interface Message Processor (IMP) routers, although the term "router" had not yet been coined.
The first testing of live ARPANET components started on August 30, 1969, when BBN delivered the first customer IMP to an ARPANET site (Leonard Kleinrock's lab at UCLA). A one-IMP ARPANET was still meaningful, because it allowed testing of the host computer interface to the IMP. Installation of the second IMP at the Stanford Research Institute (SRI) on 29 October 1969, and testing of IMP-IMP protocols began: the first wide-area routing system.
Among the first applications on the experimental networks was email, on the ARPANET as well as vendor-proprietary networks and early commercial packet-switching networks such as TELENET and TYMNET. The latter networks used the X.25 protocol that mimicked telephone calls, creating paths for each sender-receiver connection, as opposed to the connectionless Internet Protocol and its ancestors. Commercial email networks using X.25 were operational in 1972.
- DARPA
- BBN - Bolt, Beranek and Newman
- NCP (ARPANET)
Hypertext had been invented by Ted Nelson around 1960, and hyperdocuments could be transferred as files; Tim Berners-Lee later pioneered dynamic access to hyperdocuments on servers, which was the start of the World Wide Web.
1975 to 1980
In 1979, the National Science Foundation established CSNET, to interconnect academic computer science departments and research institutions that were not eligible for ARPANET access.
1980 to 1985
Tim Berners-Lee, while a consulting engineer at CERN, wrote, for personal use, a program called Enquire. Enquire can reasonably be considered the first networked hypertext application, although it certainly did not have the extensive indexing structure that characterizes the modern Web.
Specifically military research split off the ARPANET into MILNET in 1983, although there was controlled access, mostly from military to nonmilitary. Email could still pass fairly freely. There were a wide range of internal military networks using the technologies being researched. The research networks had their results shared, but the operational networks tended to suffer from the urban legend that people told about them had to die.
Without any intended Orwellian symbolism, the early, experimental ARPANET. in 1984, evolved to the NSFNET, originally a U.S. government funded network that linked five supercomputer centers. At these centers, authorized research and academic users could connect their networks and access both the supercomputers and other resources. [8] The centers were interconnected by what seemed, at the time, to be extremely fast 56 Kbps lines; 9.6 Kbps lines had been more of a limit for most other installations
1985 to 1990
NSFNET did not allow commercial traffic, but there was a gradual creation of networks, often simple pairings, of various computers and networks over which traffic ineligible for the NSFNET passed. In the early nineties, an increasing number of IP networks were commercially available, which connected to one another, and to NSFNET, in many ways both official and unofficial.
Nevertheless, the Internet routed approximately same packets as today. The Internet of the time was not a public resource, and the research and academic users collaborated productively using electronic mail, file transfer, news, and other services.
Before AOL opened up USENET and other Internet resources in the late 80s, the Internet was first an environment for networking research, and second an environment to support other research and education. When anonymous access became common, the social environment changed radically. The environment was one of trust as well as collaboration; anonymous access was rare.
Malware such as worms and viruses were rare; the first well-known breakin happened in 1986,[9] and the Morris worm hit in 1988.[10]
1988 saw a major speed increase in NSFNET, going from what were then powerful and expensive 56 Kbps lines to 1.5 Mbps links more than 24 times faster.
Tim Berners-Lee made the first proposal, in 1989, for the beginnings of a recognizable World Wide Web, based on his 1980 research on networked hypertext, which built on Ted Nelson's 1960 research on local hypertext.
1990 to 1995
The ARPANET was officially turned off in 1990, but with many replacement networks. In 1990-1991, the general experience was that traffic, and especially the number of new network routes, was doubling approximately every five months, but router capacity was doubling every 18 months. Classless inter-domain routing (CIDR), a variant of IP, bought time for routers to catch up, by making routing more efficient. By 1995, Version 4 of the Border Gateway Protocol, which fully supported CIDR, was operationa.
NSFNET, which had essentially given up the Acceptable Use Policy of no commercial traffic, shut down in 1995. The National Science Foundation did create a new restricted IP network for supercomputing and high performance networking research, the Very High Speed Backbone Network Service (vBNS).
Impact on Society
Netiquette
References
- ↑ Pouzin, L. (May 1974), A Proposal for Interconnecting Packet Switching Networks, Bronel University, at 1023-36
- ↑ Defense Advanced Research Projects Agency. United States government (2003). Retrieved on 2007-05-12.
- ↑ Internet Pioneers: J.C.R. Licklider
- ↑ Cerf, Vint (July 1978), The Catenet Model for Internetworking, IEN 48
- ↑ Baran, Paul (1964), On Distributed Communications: I. Introduction to Distributed Communications Networks, Rand RM-3420-PR
- ↑ Strategic Automated Command Control System
- ↑ Williams, Carla (17 November 2005), Minot completes final MEECN modifications
- ↑ 8.0 8.1 National Science Foundation, The Launch of NSFNET
- ↑ Stoll, Cliff (1989), The Cuckoo's Egg: Tracking a Spy Through the Maze of Computer Espionage, Pocket
- ↑ , Security of the Internet, The Froehlich/Kent Encyclopedia of Telecommunications vol. 15., Marcel Dekker, 1997, at 231-255