User:David MacQuigg/Sandbox/Email security: Difference between revisions
imported>David MacQuigg No edit summary |
imported>David MacQuigg No edit summary |
||
| Line 1: | Line 1: | ||
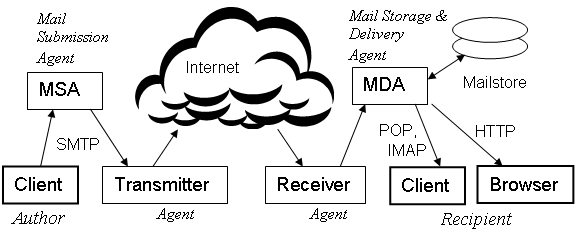
This article on '''Email security''' provides a brief overview of the ways in which email systems may be abused, and the techniques that are most effective in fighting that abuse. We | This article on '''Email security''' provides a brief overview of the ways in which email systems may be abused, and the techniques that are most effective in fighting that abuse. We classify the vulnerabilities according to their locality in Figure 1 of [[Email system]], repeated here for convenience. We assume the reader is familiar with that article. | ||
{{Image|EmailSystem.png|center|700px|'''Figure 1 Actors (Users and Agents) and their roles in an ideal email system.'''}} | {{Image|EmailSystem.png|center|700px|'''Figure 1 Actors (Users and Agents) and their roles in an ideal email system.'''}} | ||
| Line 10: | Line 10: | ||
1) [[trained]] to '''not run''' any programs that may infect their computer.<br /> | 1) [[trained]] to '''not run''' any programs that may infect their computer.<br /> | ||
2) required to maintain [[secure passwords]]. | 2) required to maintain [[secure passwords]]. | ||
Note: These requirements are only guidelines. The same level of security may be provided in some other way. For example, there is no need for passwords if every user can be authenticated by their address on a local network, secure from any outside intruder. | |||
== MSA vulnerabilites == | == MSA vulnerabilites == | ||
An MSA may be tricked into relaying mail from an unauthorized source, or from an authorized source that has been compromised. Some | An MSA may be tricked into relaying mail from an unauthorized source, or from an authorized source that has been compromised. Some large mail services, eager to get new accounts, may allow criminals to sign up for free accounts. | ||
'''MSA agents should:'''<br /> | '''MSA agents should:'''<br /> | ||
1) [[authenticate]] any user attempting to submit an email.<br /> | 1) [[authenticate]] any user attempting to submit an email.<br /> | ||
2) require their users to maintain [[secure passwords]].<br /> | 2) require their users to maintain [[secure passwords]].<br /> | ||
3) treat new accounts with special caution, ensuring that the benefits of abuse are less than the cost of establishing | 3) treat new accounts with special caution, ensuring that the benefits of abuse are less than the cost of establishing new accounts.<br /> | ||
== Transmitter vulnerabilites == | == Transmitter vulnerabilites == | ||
Criminals never use their own identity in malicious transmissions. They will either make up a new identity, or forge the identity of a trusted domain. Criminal use of a trusted name provides better access to victim systems, and damages the reputation of the trusted name. | Criminals never use their own identity in malicious transmissions. They will either make up a new identity, or forge the identity of a trusted domain. Criminal use of a trusted domain name provides better access to victim systems, and damages the reputation of the trusted name. Domain owners who care about their reputation should ensure that their Transmitter agent is honest and competent. | ||
'''Transmitter agents should:'''<br /> | '''Transmitter agents should:'''<br /> | ||
1) publish a list of IP addresses for their [[authorized transmitters]] (outgoing Border MTAs).<br /> | 1) publish a list of IP addresses for their [[authorized transmitters]] (outgoing Border MTAs).<br /> | ||
1a) work with their MSA agents to publish additional authentication information helpful in their business situation. This could include public keys used in [[digital signatures]] or information used to [[authenticate specific message headers]].<br /> | 1a) work with their MSA agents to publish additional authentication information helpful in their business situation. This could include public keys used in [[digital signatures]] or information used to [[authenticate specific message headers]].<br /> | ||
2) implement [[rate limits]] on outgoing mail from each user account | 2) implement [[rate limits]] on outgoing mail from each user account.<br /> | ||
2a) work with their MSA agents to provide additional security as needed in their situation. This could include analyzing the content of messages, providing alerts to anyone who might be an innocent source of abuse.<br /> | 2a) work with their MSA agents to provide additional security as needed in their situation. This could include analyzing the content of messages, or providing alerts to anyone who might be an innocent source of abuse.<br /> | ||
3) respond promptly to reports of abuse, even if their transmitters are not responsible. | 3) respond promptly to reports of abuse, even if their transmitters are not responsible.<br /> | ||
4) maintain a good reputation for the identities used by their transmitters.<br /> | 4) maintain a good reputation for the identities used by their transmitters.<br /> | ||
5) comply with all standards relating to their operations, thus allowing receivers to avoid mistakes affecting security.<br /> | 5) comply with all standards relating to their operations, thus allowing receivers to avoid mistakes affecting security.<br /> | ||
6) handle bounce messages (Delivery Status Notifications) in a way that provides maximum reliability while avoiding abuse. This could include adding validation codes to the Return Address on every message.<br /> | 6) handle bounce messages (Delivery Status Notifications) in a way that provides maximum reliability while avoiding abuse. This could include adding validation codes to the Return Address on every outgoing message.<br /> | ||
Revision as of 21:18, 10 September 2009
This article on Email security provides a brief overview of the ways in which email systems may be abused, and the techniques that are most effective in fighting that abuse. We classify the vulnerabilities according to their locality in Figure 1 of Email system, repeated here for convenience. We assume the reader is familiar with that article.
Client vulnerabilities
After running a malicious program, perhaps from a phony website or attached to an email, the user's computer may become infected with a zombie program controlled by a remote criminal system. This can result in stolen passwords or the loss of other personal and financial data, or the sending of spam from the user's computer.
Users should be:
1) trained to not run any programs that may infect their computer.
2) required to maintain secure passwords.
Note: These requirements are only guidelines. The same level of security may be provided in some other way. For example, there is no need for passwords if every user can be authenticated by their address on a local network, secure from any outside intruder.
MSA vulnerabilites
An MSA may be tricked into relaying mail from an unauthorized source, or from an authorized source that has been compromised. Some large mail services, eager to get new accounts, may allow criminals to sign up for free accounts.
MSA agents should:
1) authenticate any user attempting to submit an email.
2) require their users to maintain secure passwords.
3) treat new accounts with special caution, ensuring that the benefits of abuse are less than the cost of establishing new accounts.
Transmitter vulnerabilites
Criminals never use their own identity in malicious transmissions. They will either make up a new identity, or forge the identity of a trusted domain. Criminal use of a trusted domain name provides better access to victim systems, and damages the reputation of the trusted name. Domain owners who care about their reputation should ensure that their Transmitter agent is honest and competent.
Transmitter agents should:
1) publish a list of IP addresses for their authorized transmitters (outgoing Border MTAs).
1a) work with their MSA agents to publish additional authentication information helpful in their business situation. This could include public keys used in digital signatures or information used to authenticate specific message headers.
2) implement rate limits on outgoing mail from each user account.
2a) work with their MSA agents to provide additional security as needed in their situation. This could include analyzing the content of messages, or providing alerts to anyone who might be an innocent source of abuse.
3) respond promptly to reports of abuse, even if their transmitters are not responsible.
4) maintain a good reputation for the identities used by their transmitters.
5) comply with all standards relating to their operations, thus allowing receivers to avoid mistakes affecting security.
6) handle bounce messages (Delivery Status Notifications) in a way that provides maximum reliability while avoiding abuse. This could include adding validation codes to the Return Address on every outgoing message.